Leading Brands Trust Digital Element






Leading the IP Geolocation space for over 20 years
For over 25 years, Digital Element has empowered businesses with cutting-edge IP address intelligence and geolocation solutions. We leverage multiple data sources, hold over 50 patents, and partner with the top ISPs and networks. Additionally, we process billions of IP observations daily to ensure our clients have access to the most accurate and comprehensive IP address intelligence available.
Drive better results with unparalleled accuracy and coverage
Achieve unmatched accuracy and precision in IP geolocation, with detailed accuracy to postal code and ZIP+4 levels worldwide. Global accuracy is more than 97% at a city and 99.99% at the country level.
This is complemented by extensive internet coverage of 99.9999%, covering both IPv4 and IPv6 addresses.
Improve insights with the most comprehensive IP address intelligence
Geolocation is only the beginning. Digital Element’s patented approach uncovers rich contextual information to support advanced applications in targeted advertising, content customization, compliance, fraud detection, cybersecurity, digital rights management, and more.
From VPN and Proxy detection, to IP Address stability and range – Digital Element offers the most comprehensive IP Intelligence dataset available.
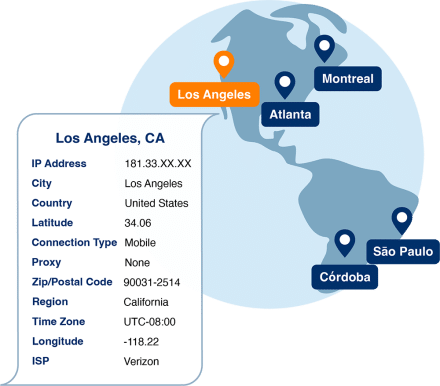
Get expert guidance for your use case
With over 25 years of experience in leveraging IP address intelligence and geolocation for diverse applications across numerous industries, our seasoned engineers are dedicated to providing the consultative guidance to amplify insights and deliver the competitive edge your business needs to excel.
Versatile data for diverse use cases
Unlock the power of IP address intelligence and geolocation data with solutions tailored to your business's unique needs.

Content Localization
Personalize user experiences by tailoring content, language, currency, and other characteristics.
Targeted Advertising
Improve ad conversion rates with improved segmentation and geo-targeted ad delivery.

Digital Rights Management
Manage the accessibility of online content and protect digital assets against online piracy.
Online Fraud Detection
Successfully detect and prevent online fraud by leveraging geolocation information and proxy detection.
Location Analytics
Identify high-engagement regions, analyze location-specific activities, and discern real users from fraudulent ones.
Mobile User Targeting
Serve customized and localized content to mobile consumers who access the Internet from either Wi-Fi hotspots or wireless networks.
Digital Element Spotlight

The Definitive Guide to Understanding IP Address and VPN Intelligence
Discover how teams in Cybersecurity, Adtech, Compliance, DRM, and more can leverage rich insights from IP addresses and VPN Intelligence to drive smarter decision-making.

Digital Element Named “Data Solution of the Year for Marketing” in 5th Annual Data Breakthrough Awards Program
Prestigious International Awards Program Recognizes Outstanding Data Technology Products and Companies

The @exchangewire Industry Review 2024 is out!
Our VP, Int’l, Charlie Johnson gives 4 actions marketers should take and the questions to ask along the way when diving into the post-cookie digital world.